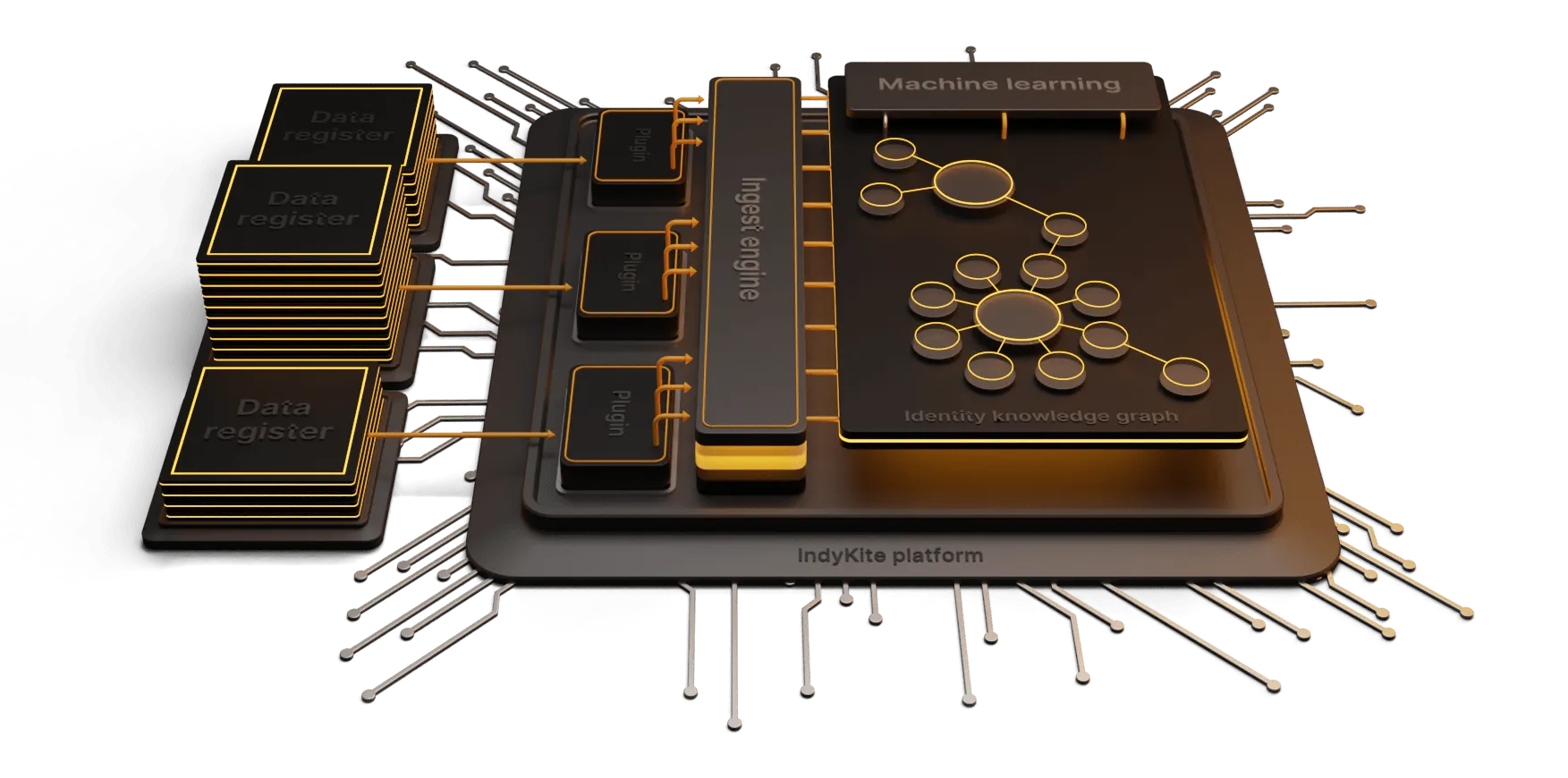
Understanding Identity Management
Identity management, is the process of establishing and managing a user's digital identity across various systems and applications. While there is a specific framework for workforce identity management, identity management extends beyond the workforce to include customer identity and access management (CIAM). CIAM is a specialized branch of identity management focused on managing and securing the identities of customers, partners, and other external users who interact with an organization's digital services and applications.
Key Components of Customer Identity Management:
- Onboarding and provisioning: The first step in CIAM is to allow customers to register and create their digital identities. During the onboarding process, customers provide necessary information, such as usernames, email addresses, and contact details, which will be used to create their accounts.
- Identity Verification: CIAM platforms may include identity verification mechanisms to ensure that customers' identities are genuine and to prevent fraudulent account creations.
- Consent Management: managing the user’s preferences in regard to data sharing is a crucial although relatively new feature of CIAM. Granular consent management, enables customers to grant or revoke permissions for the use of various aspects of their data. Sharing data will often enhance their experience however this must be managed in a compliant way. Learn more about Trusted Data Sharing here.
- Identity orchestration: To maintain consistent security and customer experience customer identities should be connected across different systems and applications
- Identity Lifecycle Management: This encompasses managing a user's identity from onboarding, maintenance and eventual offboarding (if they cancel their account or remove the association).
- Customer Analytics: CIAM solutions can provide insights into customer behavior and preferences through analytics. These insights can help organizations tailor their services and marketing efforts to better serve their customers
Understanding Access Management
Access management, also known as authorization or privilege management, is a feature of identity management and refers to the process of controlling who can access specific resources, systems, or data.
Key Components of Access Management:
- Authentication: This process verifies a user's identity to ensure they are who they claim to be. It typically involves username and passwords, along with additional factors of authentication. Passwordless and biometric authentication are becoming more popular.
- Authorization: Once a user is authenticated, access management determines the appropriate level of access they should have and what they can do within a system or application.
- Access Control: Access management implements controls to enforce the level of access granted (which determines what a user is authorized to access and do). These controls can be granular or coarse and consist of policies that are constructed from single or multiple attributes. A coarse grained approach would be role-based access control (RBAC), medium grained would involve a combination of attributes such as policy or attribute based access control (PBAC or ABAC), whereas a fine grained approach would involve contextual data as well as attributes such as Knowledge Based Access Control (KBAC).
Both identity management and access management are integral components of a robust cybersecurity strategy. Implementing modern identity management that uses granular access controls will enhance your cybersecurity posture, and ensure the confidentiality, integrity, and availability of sensitive information in an increasingly interconnected world.