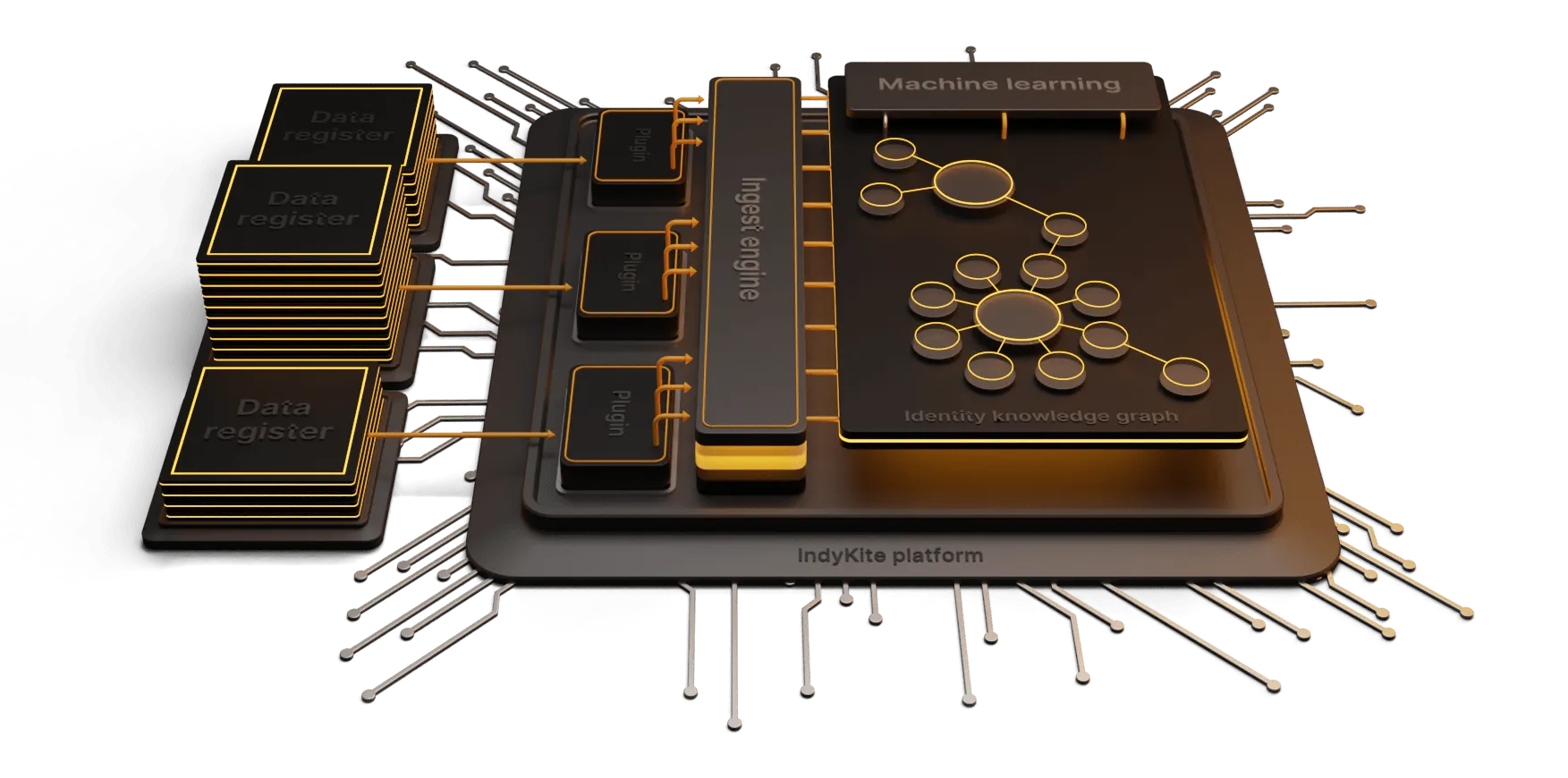
The Evolution of Identity and Access Management
Traditional IAM systems operated in isolation, leading to fragmented security protocols and inconsistent user experiences. However, the advent of connected data has ushered in a new era of IAM, characterized by a seamless integration of user identity information and access privileges across diverse systems and platforms. By establishing a unified framework, connected data optimizes access management, ensuring consistency, precision, and security throughout the organization's digital ecosystem.
Unifying User Identities and Access
The concept of connected data revolves around the interlinking and synchronization of user identity details and access permissions across multiple applications and databases. This integration empowers organizations to centrally administer access while upholding accuracy and coherence of user information. Through this holistic approach, connected IAM systems deliver a user-friendly, secure experience, augment visibility into access patterns, and streamline the complete identity lifecycle management process.
Enhanced Security through Contextual Awareness
Connected data introduces a layer of contextual intelligence to IAM systems, revolutionizing access authorization. By analyzing factors such as user location, device type, time of access, and recent interactions, IAM systems equipped with connected data can efficiently differentiate legitimate access requests from potential security breaches. This contextual insight acts as a proactive defense mechanism, mitigating unauthorized access risks and bolstering overall cybersecurity posture.
Improved User Experience
Dynamic, contextualized and real time data means you can limit the friction for the user and drive great experiences that the user loves. Further, the identity data can be queried for further use, such as for recommendation engines and personalizations.
Flexibility
The flexible nature of a connected data model, means that you can adjust your data structure as you scale, without risk of unintentional breakdowns or accidental architectures to manage. In an authorization context, this flexible model also allows you to adjust your access policies as new data points or data types are ingested.
Business value
Data is gold, and connected data models capture rich knowledge that will continue to grow as your users engage and share data with you. This data can then be queried to uncover deep insights, develop new solutions and ultimately enable new identity use cases that can drive value for your business.
Efficient Identity Lifecycle Management
Successful IAM encompasses comprehensive identity lifecycle management, spanning onboarding, role transitions, and offboarding. The integration of connected data streamlines this process, enabling organizations to update user information and access permissions centrally, which are then seamlessly propagated across all interconnected systems. This cohesive approach guarantees the accuracy and timeliness of user access, mitigating the risks posed by obsolete data or unauthorized accounts.
How to get started with connected data for IAM
Individually, each of these advantages possesses the potential to serve as a potent distinguishing factor, propelling growth in competitive markets. Together, they are game changing for your organization, commercial prospects and your end user.
Most businesses have already made substantial investments in IAM solutions, while simultaneously managing a multitude of legacy systems. Ripping out the old to make way for the new is often painful, out of scope and altogether unachievable.
The final benefit to understand with a connected data IAM solution, is that it can be fully integrated and connected to your existing stack. No rip and replace required, and as it can leverage data from your current systems, you can actually extend the value of your existing investment.
Interested in learning more? Get in touch with the team, or check out our recent webinars.