While these are not new challenges, the complexity of the modern digital world pushes beyond the capacity of current methods and solutions. The threat landscape has also evolved: remote workforces continue to rise along with, bring your own device (BYOD) and the rise of IOT and smart devices. This has led to expanding boundaries for conducting business as well as an expanding attack surface.
To manage this, many organizations have moved towards a zero-trust model that restricts unauthorized access from outside but also from within the organization - making identity the new perimeter.
With identity at the heart of the threat landscape and also the key defense focus, Gartner has named identity-first security as one of the top security and risk management trends. An effective identity-first approach can’t forget the customer amidst the threat landscape and must enable smooth access to the right people at the right time for the right reasons.
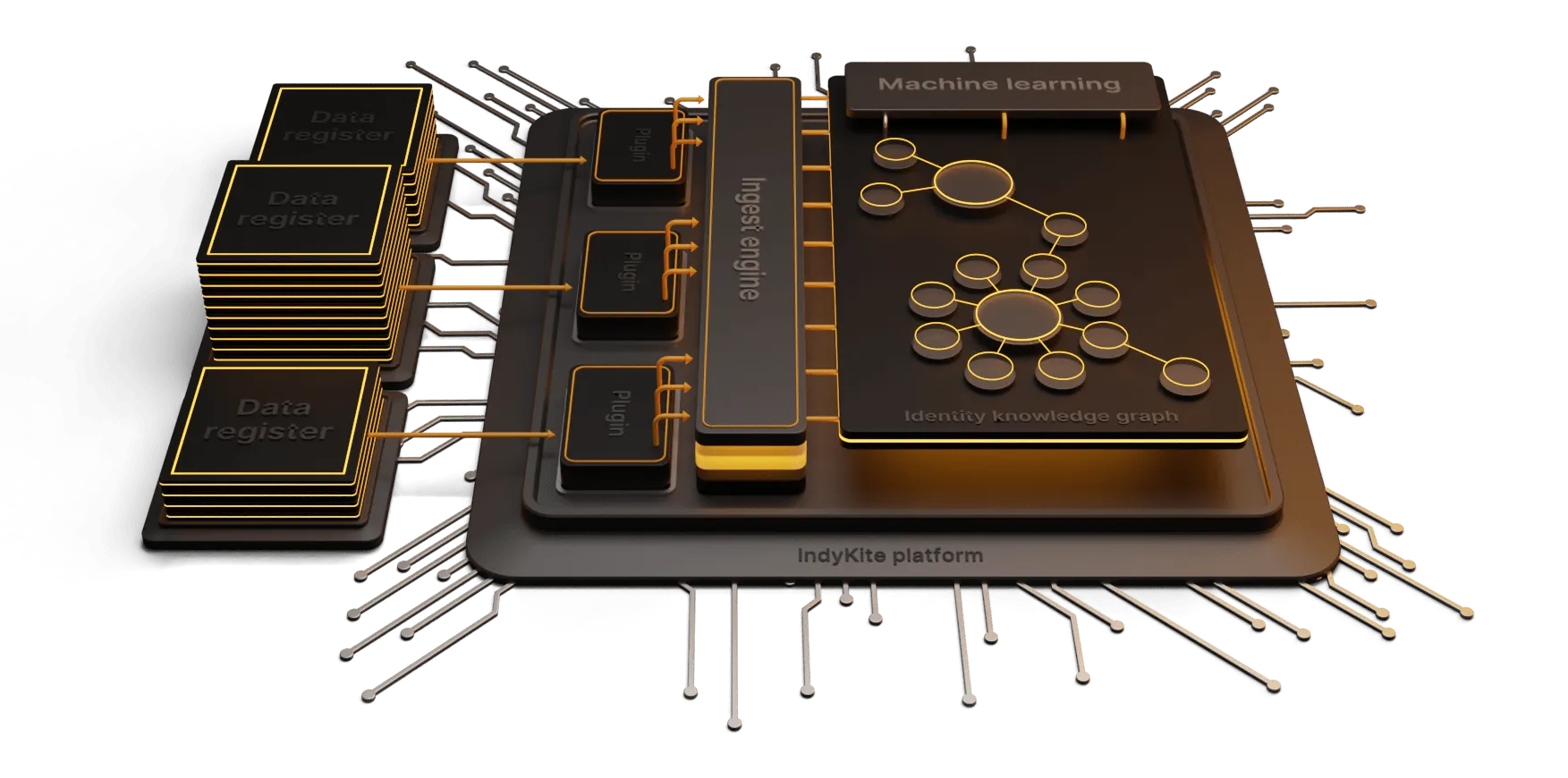
Traditional CIAM models have focussed heavily on secure authentication with authorization policies and decisions inbuilt into the applications themselves. Graph-driven CIAM provides a centralized view of the identity data to enable dynamic and orchestrated customer interactions, and authorization decisions, while also making the data available to support analytics and intelligence functions. This enables that smooth experience for the customer while also enhancing threat detection and response.
The magic is in how the flexible data model works to operationalize the data.
Mapping Complex Relationships
Graph databases excel at representing complex relationships by mapping the connections between customer profiles, attributes, devices, programs etc. This map provides a rich view of your customer base with dynamic data points. This enhances your ability to identify potential risks, such as unauthorized access attempts, suspicious behavior, or identity theft, with greater accuracy and speed.
Real-time Access Analytics
Graph facilitates real-time access analytics by capturing and analyzing real-time data such as customer interactions with various systems and services. This allows you to detect patterns, anomalies, and potential risks in customer behavior enabling a swift response to potential security threats, and mitigation of risks proactively. Additionally, graph algorithms can simulate risk scenarios, aiding in proactive risk management strategies.
Adaptive Customer Identity Governance
Graph technology enables dynamic and adaptive governance of customer identities. Traditional CIAM systems often struggle to keep pace with evolving customer profiles and access requirements. By leveraging the flexible data model, you can adjust as you go without breaking existing logic, your customers can add or change information or preferences, and your access policies can incorporate and respond in real-time to new information. This empowers you to provide seamless access experiences to customers while maintaining robust security measures, reducing the risk of unauthorized access.
Streamlined Compliance and Audit Trail
Graph technology simplifies compliance processes by providing a comprehensive audit trail of customer interactions and access activities. Every interaction, along with its associated metadata, can be captured and stored in the graph database, ensuring transparency and accountability. This feature aids in meeting regulatory requirements, such as the General Data Protection Regulation (GDPR), by offering a detailed record of customer consent, data usage, and access permissions. Graph-driven CIAM can also facilitate consent mapping of customer data sharing based on individual data points (rather than the industry standard of all-or-nothing).
Leverage the data you already have
If you are not leveraging customer identity data for risk mitigation, you have a large amount of data that is currently underutilized. Perhaps it is unavailable, buried in locked-down systems or just disconnected from your risk mitigation tooling. A graph-driving CIAM platform, like IndyKite’s can provide a unified view of your customer data and make it available for further use in your security, analytics, and intelligence workflows–without ripping out and replacing your existing stack. With simple implementation, you can leverage the data you already have to greatly enhance your risk mitigation.
Interested in learning more? Check out IndyKite’s Identity Insights Threat Detection.