It includes Authentication - using credentials to verify that you are who you say you are and authorization - what you are able to do in the system (view, edit, change, administrate).
More specifically, authorization enables trusted identities to access digital assets based on appropriate assurance levels (often within a zero trust framework). What differentiates the solutions in the market is the level of granularity involved in those authorization decisions.
Effective IAM is critical to ensuring the security of your systems and maintaining digital trust. Typically, IAM systems have been primarily concerned with maintaining security.
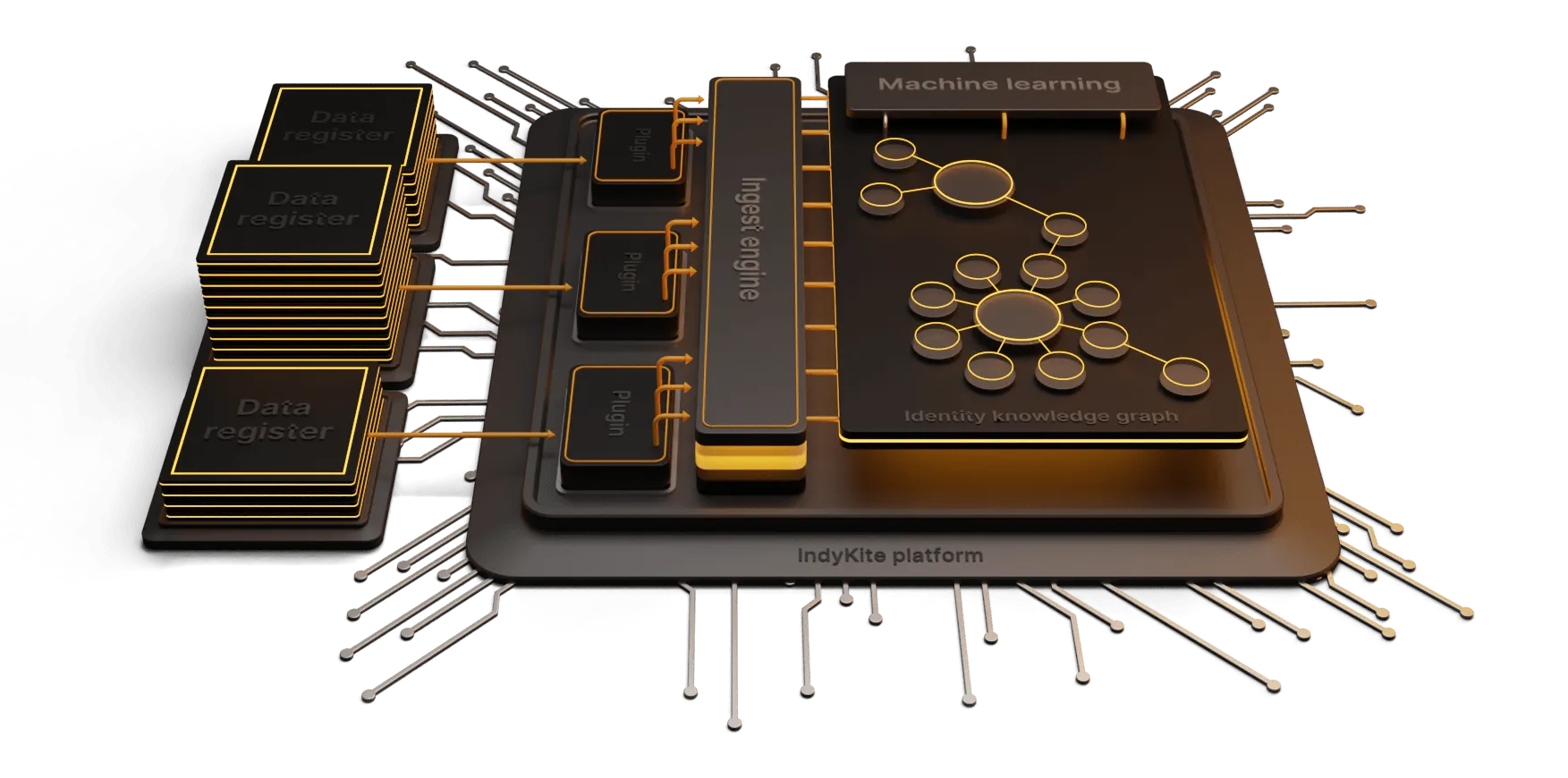
A knowledge based identity platform, like IndyKite’s, can offer more than security, giving businesses the opportunity to learn from the data and gain deeper insight to drive business growth.
Why is Identity and Access Management important
Ensuring trusted access and authorization is becoming more and more complex as more and more services, devices and things come online.
At the same time, the risk environment continues to increase with malicious actors targeting identity information and using identity as the attack vector.
Identity is foundational for establishing trust relationships, which are critical to the future of online interaction. The internet was never designed with an identity layer so there has always been a challenge of creating trusted relationships with a high degree of assurance that the person, organization or thing is who they say they are.
In the past, network security was defended at the perimeter. Now with increasing remote work forces, bring your own device (BYOD) and the rise of IOT and smart devices, the boundaries for conducting business have greatly expanded, as has the attack surface. To manage this, many organizations are moving to a zero trust model that restricts unauthorized access from outside but also from within the organization - making identity the new perimeter.
With identity at the heart of the threat landscape and also the key defense focus, Gartner has named identity-first security as one of the top security and risk management trends.
But the importance doesn’t stop there. IAM is all about your customer and their interaction with you. Every transaction, every touchpoint across platforms and products creates their experience and can either build loyalty and trust, or erode it.
A knowledge based platform can orchestrate the user’s identity across all touch points, while providing rich data that can drive personalization, service enhancement, value added opportunities etc.
Privacy is also a core concern for customers with many uncomfortable with data collection and exploitation. The right IAM platform should utilize a privacy-by-design decentralized data management model, which means users are also in control of their data, choosing when to share and what, in exchange for value creation.
Who needs identity and access management?
Any business that is allowing access to a system, whether its for staff to access shared files and systems, customer online payments, loyalty programs, or a complete virtual service.
There are few that don’t require any sort of IAM system.
Larger corporations usually choose to design their own access framework (with highly granular controls), however smaller organisations often choose an off-the-shelf-product.
As we continue to move towards Web 3.0, identity will become a critical divider between businesses that offer a good user experience (privacy, control, frictonless, etc.) and businesses that don’t.
More and more businesses are learning the value of identity orchestration across all platforms and services and it is fast becoming the new benchmark. Identity that is orchestrated will not only provide greater security, but will also provide opportunity for growth and new service development.