This heralds a new era of the internet, Web 3.0. With Web 3.0 comes new opportunities all built around connection and we will see the compound impact of connecting people, process, data, and things.
Web 3.0 will fundamentally expand the scale and scope of human and machine interactions. By cryptographically connecting data from individuals, devices and corporations, with efficient machine learning algorithms, Web 3.0 will give rise to entirely new business models.
This shift has major implications for identity management across all industries and sectors. Our interactions with other humans and things, the access privileges (or lack of) of those things - creates an enormous amount of complexity. This world requires solutions that model the complexities, and unfortunately the current ways of working don't meet those needs.
Identity management and authorization has experienced many approaches and models over the past few decades. But to really solve the challenges as well as the opportunities of the increasingly connected world, we must introduce flexible, intelligent applications. This requires a new approach to identity management, and the end of static authorization logic and fixed data models.
Ensuring the right entity is accessing the right dataset with the right credentials in the right context is a complex, distributed and multi-stakeholder identity problem.
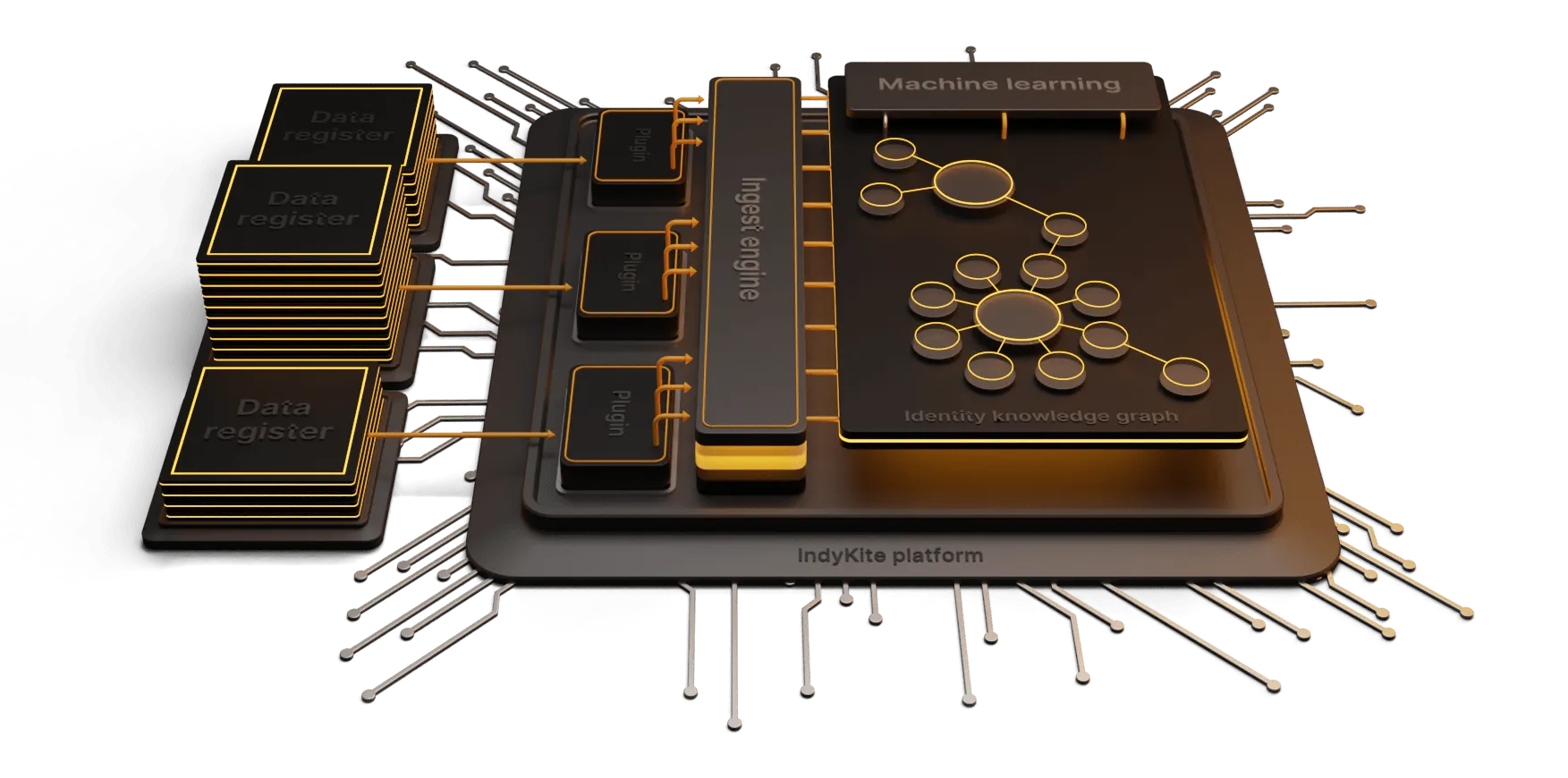
IndyKite’s Identity knowledge Graph maps and connects smart devices, OT and IT to the systems, machines, and humans in control. With this mapping you can manage every human, device, and asset identity within the enterprise and design dynamic access control and authorization.
This provides for effective and efficient identity management for humans, and IOT, but that is just the start of the value that we can achieve by using a graph driven identity approach. The contextual data held by the graph can be enriched and used to drive value across the business and enable new products and services, enhance your customer experience and create smarter solutions.
Using IndyKite’s platform, you can build identity access controls into applications, website web services and devices using simple SDKs/APIs.